
Last week, one of the largest telcos in the Asia Pacific regions was compromised. The attackers scraped customer data, including personally identifiable information (PII), via an unsecured API endpoint publicly available on the internet. The attackers released sample data of a few users, including names, email addresses, physical addresses, passport numbers, driver’s license numbers, birth dates, whether a person owns their home or not, and more. The leaked data includes both current and former customers.
Not only was the data stolen but also it was used. There were reports that driver’s licenses, passports, and national IDs were applied for on the victims’ behalf, constituting a serious risk of identity theft. A few users reported they received a direct email asking for a $2,000 ransom to delete their data.1
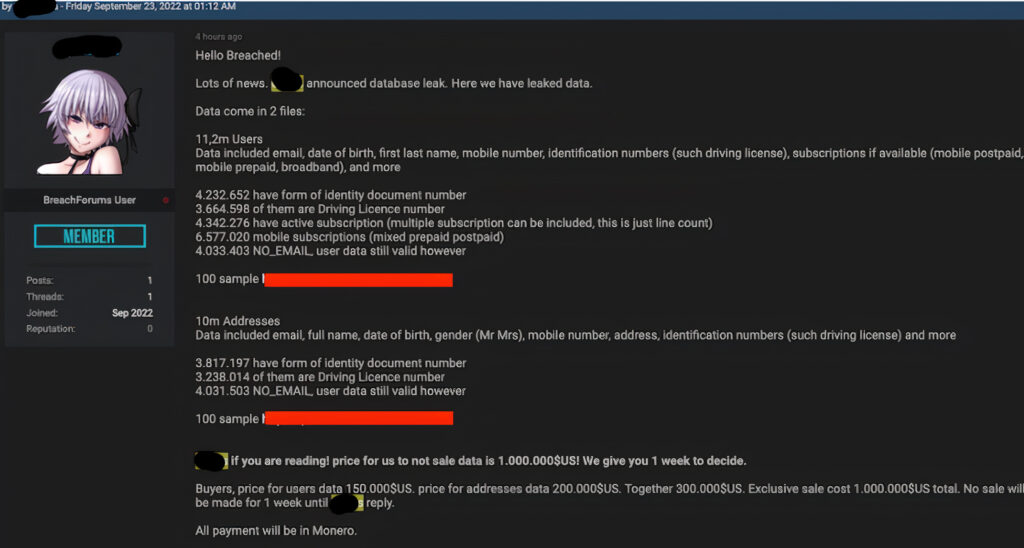
The intruders were able to fetch the data using an API that is believed to have had no authentication in place and provided direct access to the attackers for stealing the data. After leaking the data of 10,200 users, the attackers ostensibly had a change of heart and issued a public apology stating they deleted the data, however, we can only take their word as there’s no evidence to suggest they did not successfully sell the leaked data.
After a week (28-Sep-2022), the Medical Record ID for thousands were reported to be compromised via the same exposed API endpoint.2 Though this has already ignited the fire for lawmakers to impose stricter norms, proactive actions are necessary.
How can “shift-left” for API testing help?
Shift-left is an approach to software and system testing in which testing is performed earlier in the development life cycle. Developers are empowered to scan their source code and remediate identified vulnerabilities rather than relying on a separate team or process.
Traditional API protections are run-time focused, where API Gateways or Web Application Firewalls (WAFs) can only secure the API endpoints of which they are aware. In the case of the telco data breach, it appears that they were either unaware that the API endpoint existed or that it was exposed publicly, meaning an API Gateway or WAF may not have stopped the breach.
By analysing the underlying source code of the application’s APIs using static application security testing (SAST), vulnerabilities can be identified and thus remediated earlier, saving organizations time, effort, and monetary resources. And by scanning APIs at the source, organizations can identify otherwise undocumented endpoints (known as shadow APIs), such as what appears to be the case that led to the data breach of the APAC telco. Of course, you need a good platform to do the analysis.
How can Checkmarx API Security help?
The Checkmarx One™ Application Security Platform includes our API Security scan engine, which uses static code analysis to identify and inventory API endpoints, the request and response data associated with those endpoints, and any related vulnerabilities. By scanning applications and APIs at the source, we identify vulnerabilities earlier and provide pointed guidance to developers and AppSec teams on where best to address the vulnerabilities before releasing code to production.
Checkmarx API Security scans source code, indexing the data flow through the code and capturing potential vulnerabilities using a set of queries. We index, enumerate, and correlate our scan findings, providing developers and AppSec teams the specific file path and line number where the vulnerability was found. Furthermore, we provide pointed remediation guidance—as necessary—on the identified vulnerability. In the image below, we see a SQL Injection vulnerability associated with a specific API endpoint.

Because we have visibility of the underlying source code for the API endpoint, we can capture and provide details of the APIs associated parameters and whether it exposes any sensitive data, such as usernames or passwords.
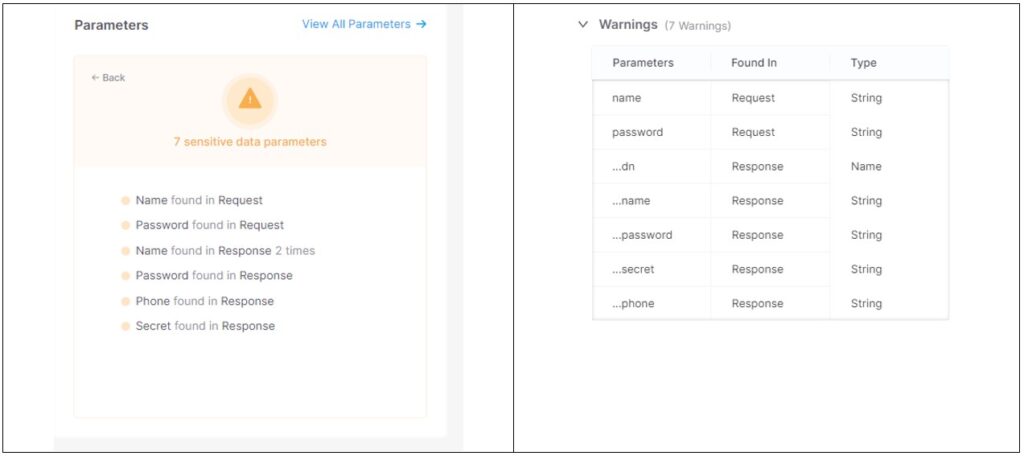
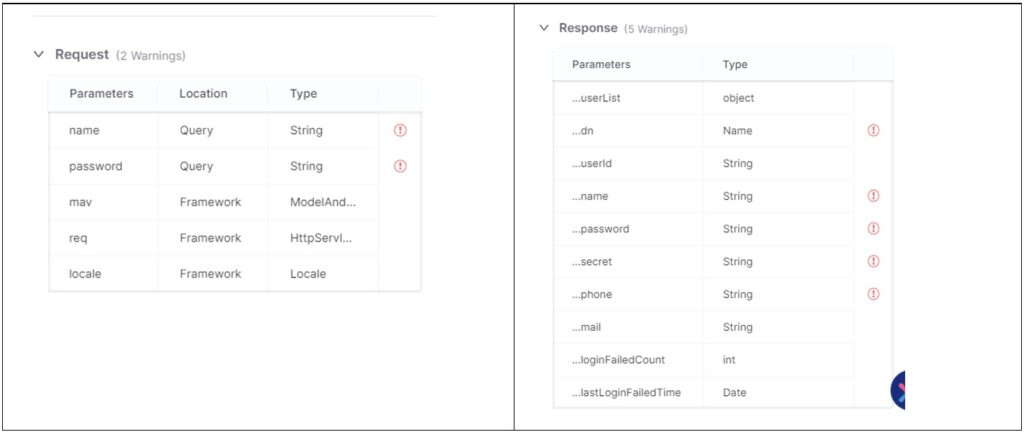
What are the benefits of using source code API security?
- Complete API visibility: Provides AppSec teams with the most accurate and up-to-date view of their entire API attack surface, eliminating the problem of shadow and zombie APIs.
- True shift-left approach: Discovers APIs in application source code to identify and fix problems earlier in the SDLC–faster with lower cost and risk.
- DevOps readiness: It can be easily integrated with DevOps platforms.
- Prioritization remediation: Focuses developers and AppSec teams on solving the most critical issues by prioritizing API vulnerabilities based on their real impact and risk.
- Holistic view into application risk: Scans the entire application with a single solution (SAST and API testing), eliminating the need for additional API-specific tools to reduce the overhead on over-burdened AppSec teams.
- Prevent vs. protect methodology: Source code analysis for API Security allows teams to create more secure APIs early in the SDLC and give fast feedback to developers, preventing issues from being pushed into the product.
- Knowing which application/project the API belongs to: reduces the time it takes to fix the problem.
Conclusion
This recent unfortunate example underscores the importance of analysing APIs at the source. By leveraging Checkmarx API Security, available within the Checkmarx One Platform, organizations can proactively protect against attacks such as these, helping to protect their customer data and reputation.
Reach out to a sales team today for more information or a live demonstration!
1 https://www.crikey.com.au/2022/09/26/optus-hack-cyberattack-reform/
2 https://www.youtube.com/watch?v=x9YIb46kPS0