
In the early days of application security, the go-to for every organization looking to secure their applications focused on two types of scanning engines only – SAST to analyze and secure source code and DAST to test against a deployed or running application.
This approach has changed in today’s AppSec world as there is a need for platform that offers a wide range of scanning engines that fit the multiple domains of modern application development, such as SAST, SCA, Infrastructure as Code, API security, etc. Also, due to the speed and complexity of modern application development, it has become imperative that any scanning engine fits seamlessly into the developer’s pipeline to not interrupt workflows or delay delivery.
And, admittedly, it is this trend of modern application development that has resulted in some AppSec experts moving away from DAST and other runtime solutions to focus on pre-deployment scanners, such as SAST and SCA.
However, this trend is about to change again. Not only does Checkmarx One offer all the scanning engines that one would expect (and then some, such as supply chain security, IaC security, and API security), but our approach to DAST is set to bring it back into the mainstream.
Getting Started with DAST
Creating Environments and Running a Scan
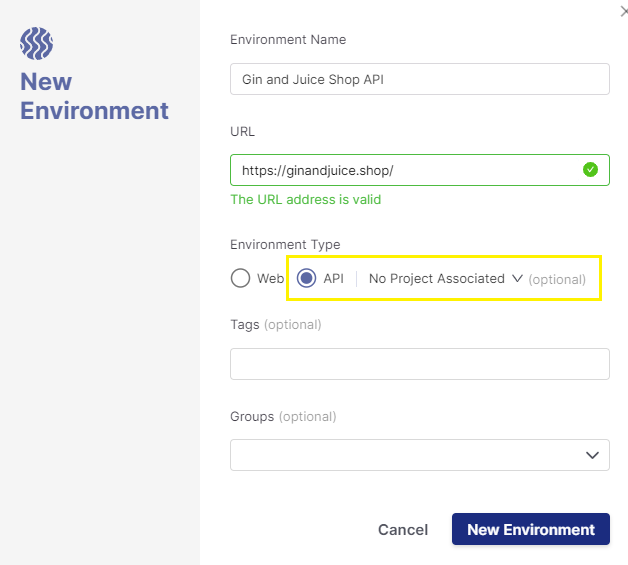
Since DAST executes against a running application, we need to create an Environment to define the application to be tested. This is where the environment’s name, URL, and type (web or API) are defined along with optional fields for tags and groups:
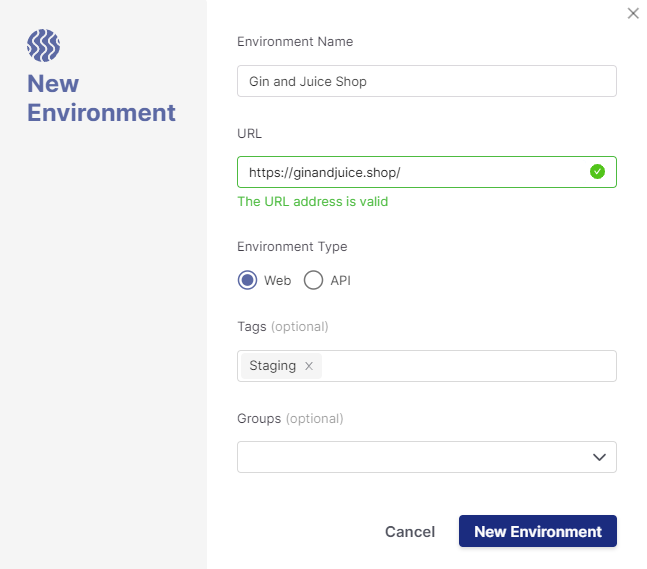
Checkmarx One supports both web and API environment types. API environments have additional fields to upload API documentation files and link the environment to a project. See the API Security Integration section for more details.
You can initiate a DAST scan either manually via the Checkmarx One portal (which we will cover in this section) or using the DAST CLI, which can be run independently or as a part of a build pipeline.
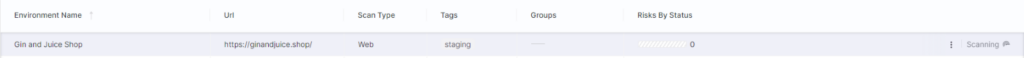
After creating the environment, it will be visible in the environments list and is ready to scan:
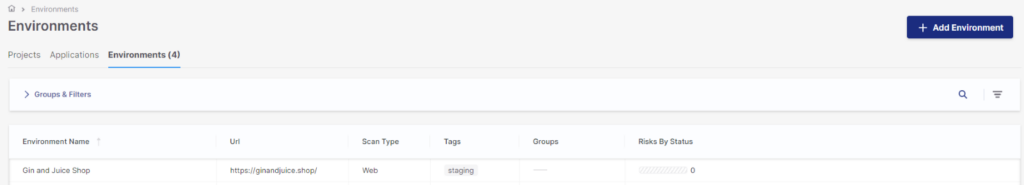
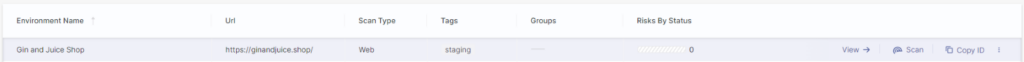
Hovering over the environment will reveal an action menu where we can start a scan, review results, and copy the environment ID (needed for pipeline integration).
Selecting the scan option will open the new scan wizard where a configuration file is provided to define scan settings, user accounts, authentication method, etc.
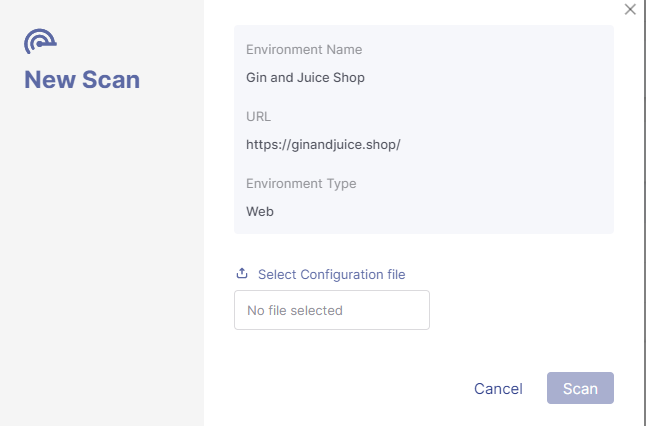
After providing the configuration file, we are ready to begin the scan:
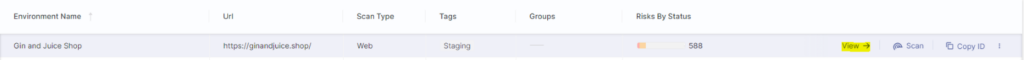
We can then use the View action to dive into the scan results:
API Security Integration
As we mentioned above, one of the key synergies in Checkmarx One is the correlation between API Security and DAST, where DAST can leverage the APIs that were discovered by API Security to drive the coverage of the DAST API scan.
It is easy for users to link a DAST API environment with a Checkmarx One project to automatically consume any API Security results. We simply need to select a project in the project drop-down:
Viewing Checkmarx One DAST Results
And finally, let’s look at how to review and triage our DAST results which we can dive into using the environment’s view option:
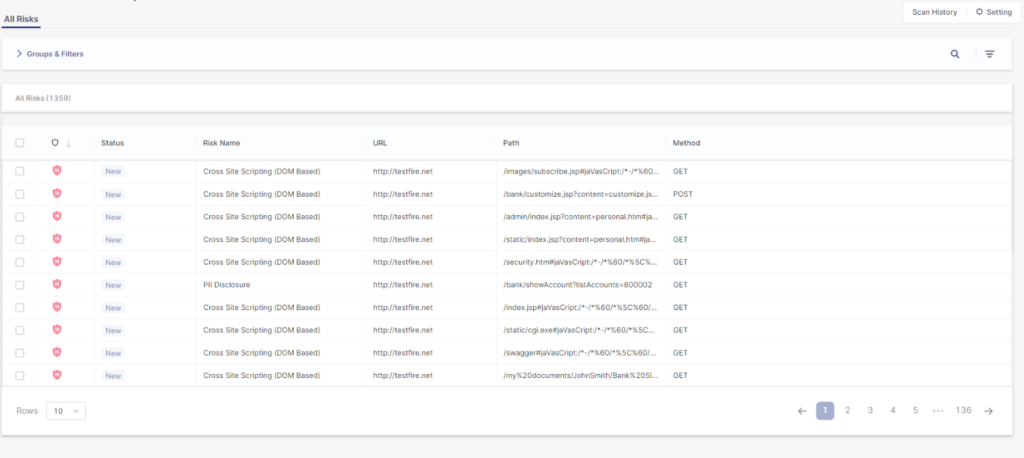
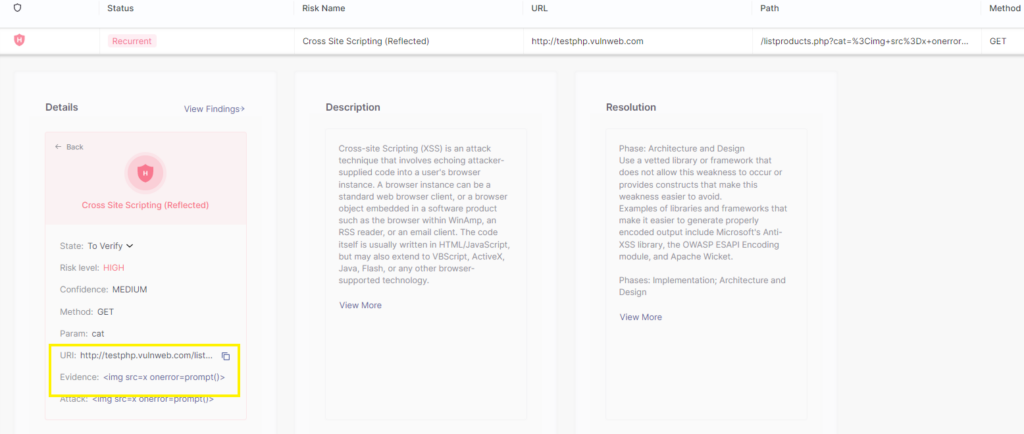
Individual findings can be investigated in detail by clicking on the issue itself. Here, on the risk detail page, we can find the more information for this vulnerability, such as its risk score, method, parameters, attack string, etc. as well as a detailed description on the vulnerability type and resolution and remediation advice:
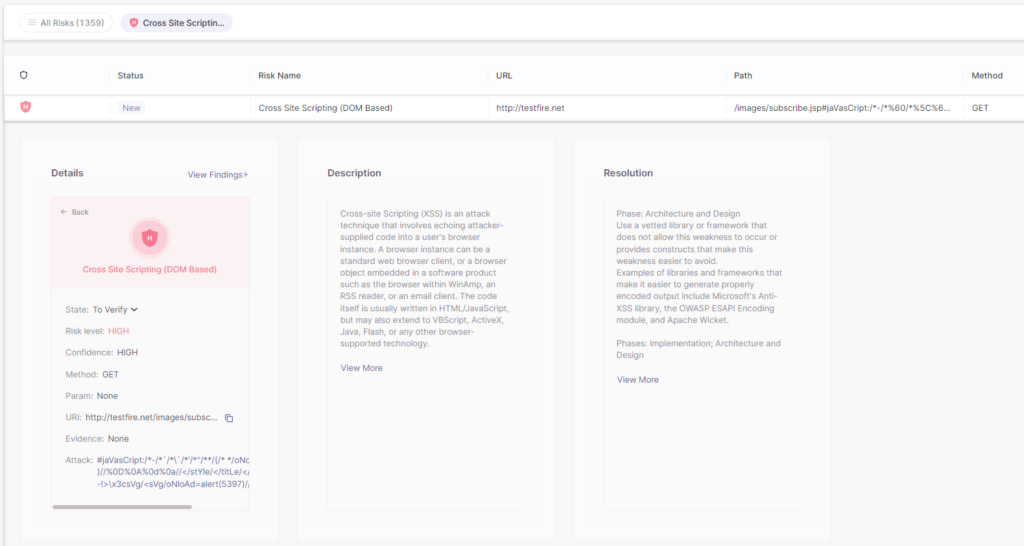
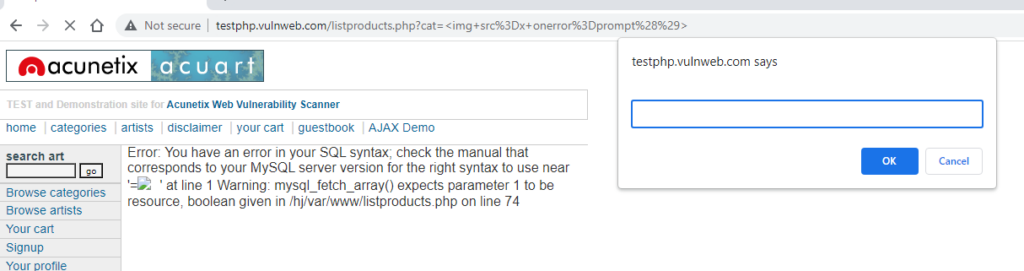
And most importantly, each DAST vulnerability also includes Evidence that has a quick link to copy the request and attack string to your local clipboard – this allows for easy validation of results:
Learn more
To learn more about Checkmarx DAST, you can see it in action here or contact your Checkmarx account team.