
Key Points
- In an ongoing campaign, a threat actor is leveraging npm packages to target developers to steal source code and secrets.
- The actor behind this campaign is suspected to be related to malicious activity dated as early as 2021 undetected.
- In this report, we will share new packages and IOCs related to this attack.
Introduction
Developers in the cryptocurrency sphere are being targeted once again, as yet another threat actor has been exposed. This user has been publishing malicious NPM packages with the purpose of exfiltrating sensitive data such as source code and configuration files from the victim’s machines.
The threat actor behind this campaign has been linked to malicious activity dating back to 2021. Since then, they have continuously published malicious code.
The latest batch of activity occurred in August, and was published by Phylum.
In this report, we will show new packages and IOCs related to this attacker. It’s important to note that we don’t just have a malicious package problem; we have an adversary problem. Only by learning attacker tactics, techniques, and procedures (TTPs), can we set up proper defenses against future attacks.
A Deep Dive Into Code
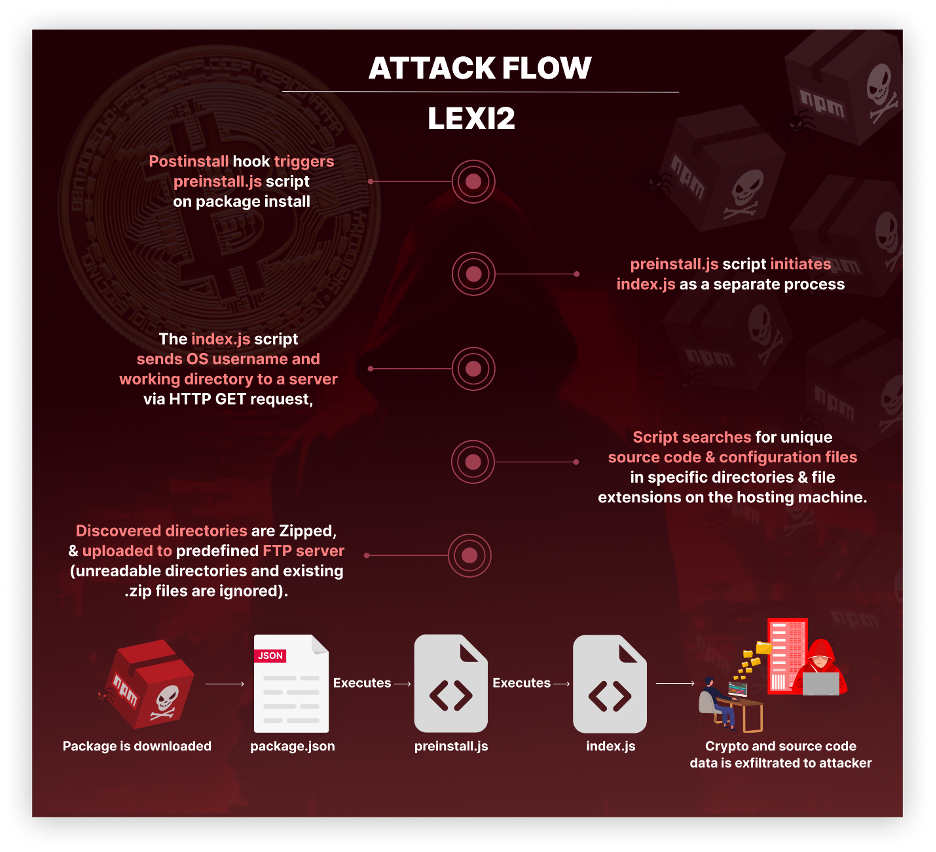
- Upon installing the malicious package, a postinstall hook defined in the package.json file triggers the preinstall.js script.
- The preinstall.js script utilizes a method called ‘spawn’ to initiate another file named index.js. Essentially, it causes index.js to run as a separate process, ensuring it continues to operate independently even after the main installation process is complete.
- The index.js script collects the current OS username and working directory and sends this information in an HTTP GET request to a predefined server.
- It then rakes through directories on the hosting machine, targeting specific directories like .env, .gitlab, and .github, and files with extensions such as .asp, .js, and .php. focusing more on unique source code or configuration files.
- Subsequently, it ZIPs the discovered directories, deliberately avoiding unreadable directories or existing .zip files.
- As a final step, it attempts to upload these archives to a predefined FTP server.
Each of the official packages used by this threat actor was designed to execute automatically upon installation. Each package contained three files – package.json, preinstall.js, and index.js. The attack flow is as follows:
The packages are tied to the cryptocurrency domain further solidifying their financial motives, with clear references to entities like CryptoRocket and Binarium.
Hunting down “lexi2” activity
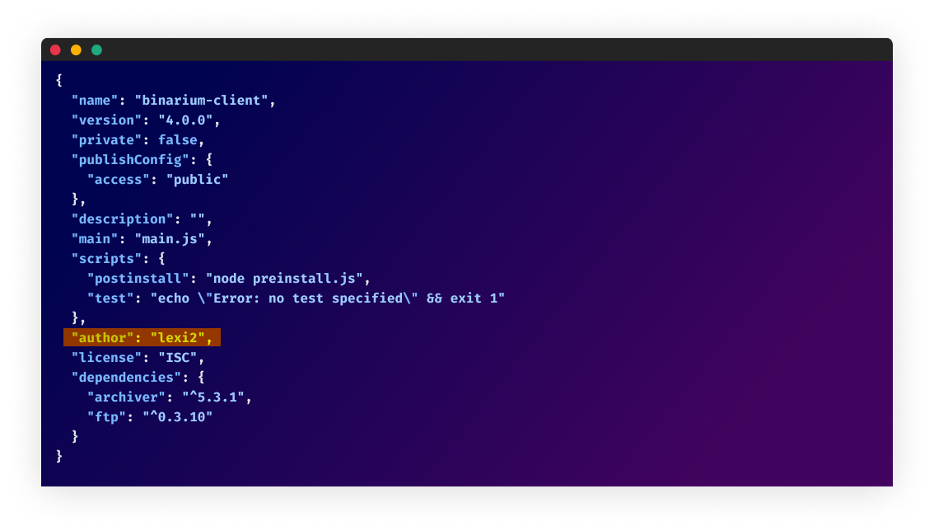
A deeper investigation revealed a consistent metadata attribute: the “author” field in the package.json file citing “lexi2″ as the author”lexi2” as the author.
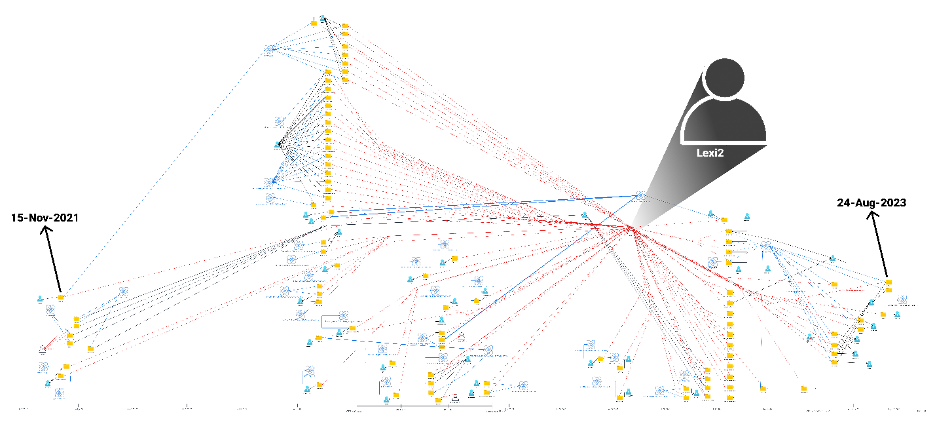
Maintaining a comprehensive data pool of all open-source packages that span different open-source repositories is critical to understanding not only the attacker, but also their evolving Tactics, Techniques, and Procedures (TTPs). Leveraging this resource, we cross-referenced “lexi2” and other code-specific attributes against dozens of additional malicious packages within our database. Our database analysis indicated that “lexi2” has been associated with malicious packages dating as far back as 2021
Addressing the Adversary Problem
We need to understand that when dealing with threat actors and especially APTs, just reporting and removing packages won’t be enough to stop them, we need as an industry to move up the “Pyramid of pain” to stop APT attackers.
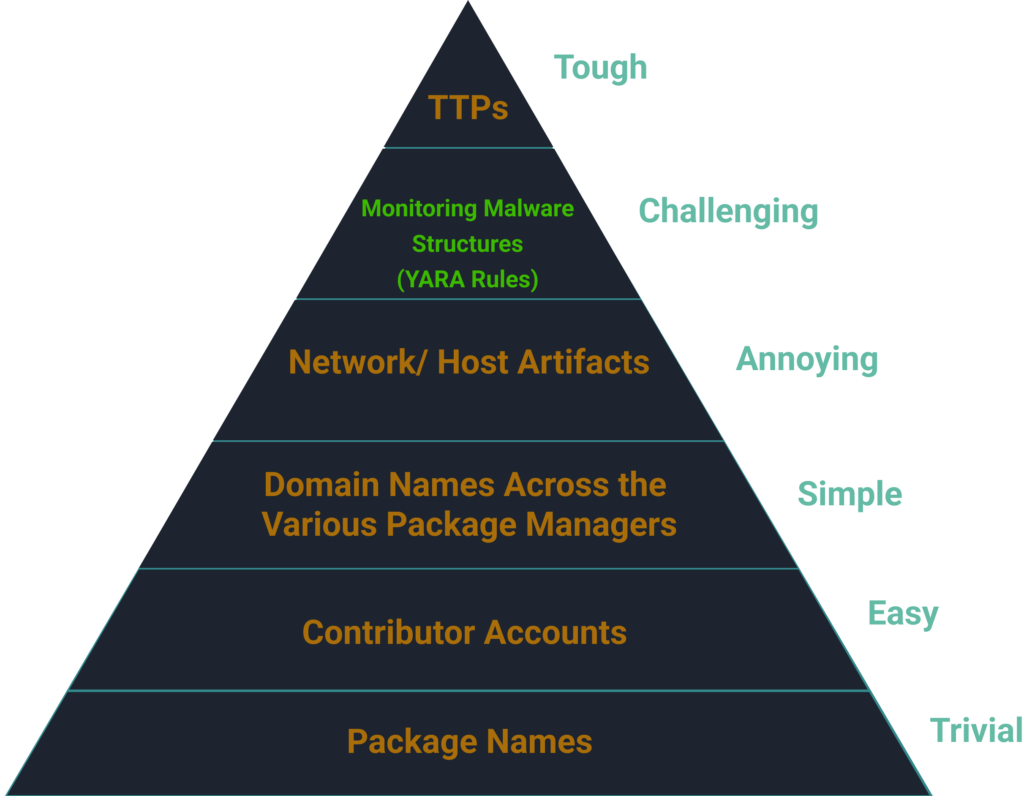
We have developed a YARA rule to aid in identifying, and preventing, the execution of the malicious scripts used in this infostealer campaign.
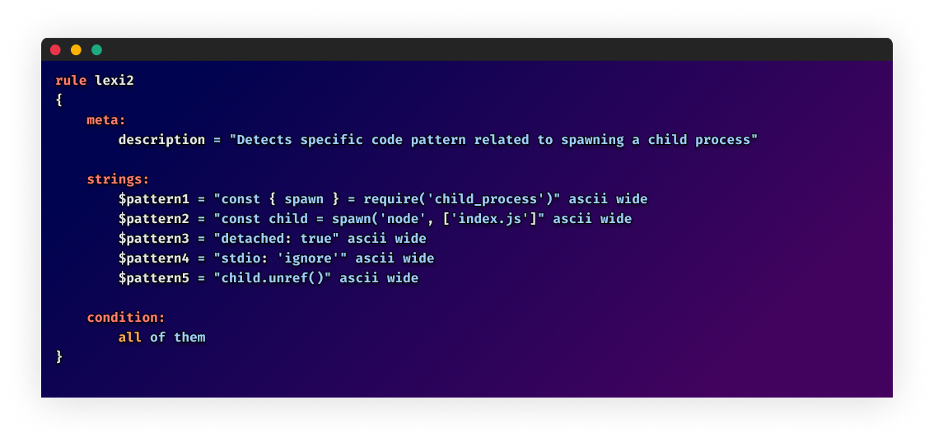
This rule, along with a continuously updated collection of threat detection signatures, can be found in our repository at os-scar/yara-signatures.
Conclusion
The cryptocurrency sector remains a hot target, and it’s important to recognize that we’re not just grappling with malicious packages ,but also persistent adversaries whose continuous and meticulously planned attacks date back months or even years.
Reactive countermeasures of deleting the most recent batch of malicious packages offer only temporary relief and don’t get to the root of the problem. Protection against these unrelenting threats requires a more sophisticated strategy.
Sharing metadata and tracking attackers is an essential component of this broader security approach. It goes beyond short-term fixes and delves into the ongoing monitoring and analysis of attacker behavior and patterns. Collaboration and intelligence sharing within the cybersecurity community can enhance our defenses, making the ecosystem more resilient to future attacks.
If you need any of these packages, feel free to contact us directly at: supplychainsecurity@checkmarx.com.
Packages
The full list of packages can be found in the following link:
https://gist.github.com/masteryoda101/01eee19e50054733dcde5b7364949550
IOCs
- 178[.]128[.]27[.]205
- 185[.]62[.]56[.]25
- 185[.]62[.]57[.]60
- 198[.]199[.]83[.]132
- 1wy3rk316x8qqy4fyxtvcs4kkbq2es2h[.]oastify[.]com
- 288utkkrohmp0nr8znflcp88nztrhg[.]oastify[.]com
- 4or5o5yn5lqzenk4[.]b[.]requestbin[.]net
- 5[.]9[.]104[.]19
- 51[.]250[.]2[.]204
- 65[.]21[.]108[.]160
- 6wxd3v84nevku06dcgbqcxrmt[.]canarytokens[.]com
- bind9-or-callback-server[.]com
- bq5m9lnmalh9ktyi9wydockt9kfb32rr[.]oastify[.]com
- c7kxnys58daceezcxx0jjstn6ec50vok[.]oastify[.]com
- cczk46g2vtc0000k68dgggx31deyyyyyb[.]oast[.]fun
- ck0r1hp2vtc00007c0zggjocy3ryyyyyb[.]oast[.]fun
- cup1qnm56sdo4bdv[.]b[.]requestbin[.]net
- efrva6[.]dnslog[.]cn
- fhg62xavat9jzyt6euwxi6sro[.]canarytokens[.]com