What exactly is the SDLC?
Organizations developing applications have in-place a process by which each application is designed, developed, tested, and deployed. This sequence of stages that define these processes is called the software development lifecycle, often referred to as the SDLC. An organization’s SDLC helps shape the way their apps are built and defines the exact processes each application should go through, as well as the milestones an application needs to hit before going to the next stage of the SDLC.
What exactly is a Secure SDLC?
A Secure SDLC is a process which has security touch points in every stage, as well as security milestones. Secure SDLC’s go above and beyond the current SDLC structure in order to ensure that the applications being deployed are secure upon release, without creating a delay in the original SDLC. The biggest advantages of organizations adopting a secure SDLC is to create a high-quality, secure product.
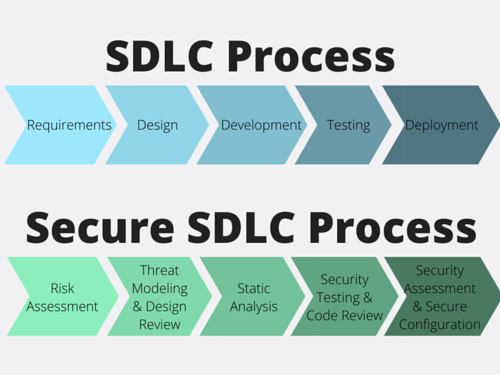
Both SDLC and Secure SDLC typically revolve around five stages, where within each stage of the SDLC (Requirements, Design, Development, Testing, and Deployment) there are security processes to be done during that time: Risk assessment, threat modeling and design review, static analysis, security testing and code review, and finally security assessment and secure configuration.
Secure SDLC within the SDLC.
Static Analysis for a Secure SDLC
Static code analysis (SCA) is one of the driving forces behind the secure SDLC philosophy after the requirements have been clearly defined and clarified to the developers. One of the biggest advantages of using static code analysis throughout the SDLC is that testing can be fully automated, enabling developers to implement secure coding practices and sanitize the whole development process with minimal effort. Product release deadlines can then be easily met without cutting corners or releasing with risky security issues. In a Secure SDLC, static code analysis tools can quickly find and help developers protect against SQL Injections, Cross-Site Scripting (XSS), Cross-Site Request Forgery (CSRF) and other malicious attacks. Without a Secure SDLC using static code analysis, there’s no assurance that an application is released without security vulnerabilities.
Best Practices for Establishing a Secure SDLC for Application Development Security:
- Create a policy of breaking the build when a medium or high-level vulnerability is discovered. Don’t put your application and organization at risk – make sure the apps you’re releasing are free of high-risk vulnerabilities.
- Understand your business and protect it with secure applications. If you know the risks that your business faces then it’s easier to develop software that protects against those risks. Application development security can offer risk prevention in the form of slowing down an approach to market (like applying the brakes in a car) or speeding it up (like pushing the accelerator) the trick is to know which is needed and when.
- Know the technology of your application. You need to consider the technology across your platform. The language of your environment may be dictated by security concerns – for example un-managed code may offer higher susceptibility to overflow attacks than managed code environments. You need to examine the hosts, network segregation and key infrastructure, in addition to the coding environment and ensure there are no obvious (or non-obvious) holes.
- Compliance is key. Ensure that compliance requirements are met through your Secure SDLC by ensuring all testing, code reviews and pen-tests are included within your process. The Secure SDLC goes beyond just security to also include governance, regulations and privacy framework compliance as required by your environment.
- Educate the developers. It’s essential that your developers understand the importance of Application Security concepts like confidentiality, integrity, availability, authentication, and authorization.
- Integration in development environment. Beyond teaching developers about secure coding practices and what their part in the Secure SDLC will be, it’s equally important to ensure the tools you choose and use are well-suited for the developer environment, integrating with as many established processes as possible.
- Source code analysis is your friend. Agile environments looking to upgrade to a Secure SDLC are the perfect place for source code analysis to be implemented. A strong source code analysis tool offers the advantages of incremental code scanning, scanning of multiple languages, quick reporting and developer assistance in mitigating vulnerabilities in their code. With source code analysis in your pipeline, applications can be secured before even being in production – though post-production, security is still highly important.
- Keep learning. Security is an evolving field. Application development security requires a constant cycle of review, education and implementation. Best practices today may not be best practices tomorrow. Most importantly it’s vital that everyone in your team recognizes that security is everyone’s job and commit to their part in this.
Why companies need to integrate security testing tools in a Secure SDLC for secure applications
Web threats are one of the largest potentially-devastating risks that companies with a web presence face today. Malware is the leading threat to companies, and the costs associated with defending from and recovering from malware attacks stretches into the billions of dollars each year. However, network security has become incredibly efficient in recent years, which has caused attackers to turn their attention to other vulnerable areas – especially the application layer. Application code with security flaws can be exploited to have devastating, unintended consequences on an organization and its’ customers. Data breaches cost companies millions of dollars annually, but software testing tools offer a helpful line of defense against such malicious attacks.